Unpacking Vulnerability Abbreviations: CVE, CVSS, CWE, CWSS…
Hello folks! It’s been a while, but here we are again trying to make sense of something new. People who have been in the security space might be thinking “have you been living under a rock?”, because the terminologies mentioned in the title aren’t brand new. In fact, the CVE system was born in 1999, just 4 years after me (yes, I am the kind of person who has no shame in announcing their age, what’s in a number eh?). The answer to that question is: Yes, I was living under a rock for all these years, but that is about to change. In this blog and a series of blogs, I am going to talk about different security terms and concepts as I learn about them, with the aim of documenting all my learnings in one place and also helping others who are on the same journey as me. So without further ado, let’s get started!

First, CVE:
According to their website, the Common Vulnerabilities and Exposures system or CVE is a program with a mission to “Identify, define, and catalog publicly disclosed cybersecurity vulnerabilities.” Over the last two decades, it has grown into an indispensable resource in the world of security, with about 180,475 records (at this time) that inform organizations, tools and services worldwide about vulnerabilities, help to uniquely identify vulnerabilities in public watch lists like the OWASP Top 10 Web Application Security Risks and form the basis for the National Vulnerability Database (NVD) , which is a “comprehensive cybersecurity vulnerability database that integrates all publicly available U.S. Government vulnerability resources and provides references to industry resources”. Funded by the US Department of Homeland Security, the MITRE corporation has copyrighted the CVE list to maintain the system. Phew, I’m out of breath. Let’s go back a few steps.
What is a vulnerability?
According to the National Institute of Standards and Technology (NIST), a vulnerability can be defined as “Weakness in an information system, system security procedures, internal controls, or implementation that could be exploited or triggered by a threat source.” To understand this, imagine that you are on a flight, watching a movie on the in-flight entertainment system over the plane’s Wi-Fi network. The entertainment system creates a sandbox environment for each passenger, allowing a passenger to watch a movie independently of other passengers use of the system. A flaw in the logic of the entertainment system can allow an attacker to break out of the sandbox and access any data stored on the entertainment system. This way, the attacker can access confidential information stored on the system, and can even modify data stored on it. The attacker might also try to repeatedly access large files, such as movies, to reduce the performance of the system and in the worst case, might even completely shut down the entire system. This is just one example. There exist several different kinds of vulnerabilities that can be exploited and a CVE record can help us in understanding each type.
CVE Record
A CVE record exists for each vulnerability. It contains identifying information about the vulnerability such as a unique CVE ID, a description of the vulnerability and at least 1 public reference. A CVE ID is assigned to a potential vulnerability by CVE Numbering Authorities (CNA), who are “software vendors, open source projects, coordination centers, bug bounty service providers, hosted services, and research groups authorized by the CVE Program to assign CVE IDs to vulnerabilities and publish CVE Records within their own specific scopes of coverage”. While a CVE record does not include risk or mitigation information, its description includes the information about the vulnerability attack type and its impact, the software components affected by it as well as any attack vectors that can make use of the vulnerability. One way to think of it is:
[PROBLEM TYPE] in [PRODUCT/VERSION] causes [IMPACT] when [ATTACK]
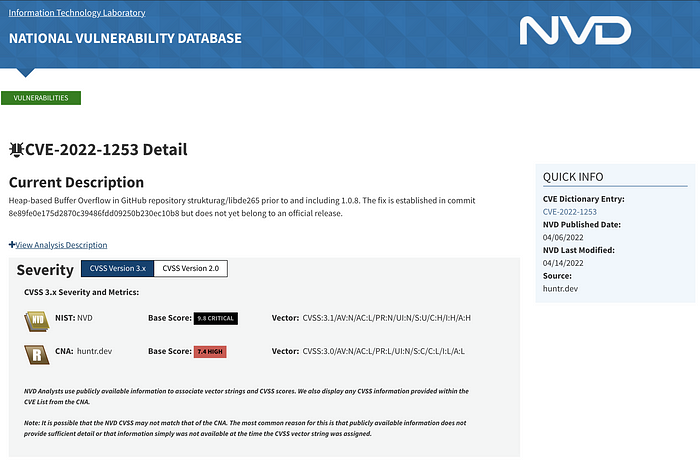
A CVE record also contains CVSS scores. The Common Vulnerability Scoring System (CVSS) “provides a way to capture the principal characteristics of a vulnerability and produce a numerical score reflecting its severity.” The numerical score ranges from 0 to 10 and can be translated into a qualitative representation such as low, medium, critical and high. This score is used by organizations to access their vulnerabilities and prioritize vulnerability management. One thing to note here is that the CVSS score is a severity score and not a risk score. For example, the CVSS score for a vulnerability might be 9.8, but it might happen that in the real-world, a vulnerability with a CVSS score of 2.8 is exploited more often than the former. So how can we prioritize the right vulnerabilities to be mitigated while ensuring that our effort is not wasted? I’ll cover that in another blog. For now, let’s look at CWE.
The Common Weakness Enumeration (CWE) is a list of common software and hardware weaknesses, classified precisely so that we can identify common patterns which can help us communicate about them.
But, Why do we need CWE when we have CVE?
If you remember, each CVE record is mapped to an individual weakness or vulnerability. CWE weaknesses are general characteristics of these vulnerabilities. For example, the CVE-2022–1253 record talks about a Heap-based buffer overflow vulnerability. This type of vulnerability belongs to CWE-787, or Out-of-bounds Write, in which “the software writes data past the end, or before the beginning, of the intended buffer.” So as you might have understood, CWE helps to describe and discuss software and hardware weaknesses in a common language. A single CWE record can provide information about many different vulnerabilities.
Since it provides information about common weaknesses, a CWE record can be used by programmers, software or hardware architects and product managers to develop solutions proactively which are free from these vulnerabilities. CWE can also help us evaluate the coverage of security tools against these weaknesses. Just like CVSS provides severity scores to CVEs, CWSS or Common Weakness Scoring System ranks the severity of CWEs. The CWE project is also operated by the MITRE corporation.
This is all that I am going to cover in this blog. In the next few blogs, let’s dive deeper into a few of these concepts, but for now, to summarize everything we discussed here:
- Common Vulnerabilities and Exposures system (CVE) is a program to identify, define, and catalog publicly disclosed cybersecurity vulnerabilities.
- A vulnerability is a weakness in a system that can be exploited.
- A CVE record exists for each vulnerability and contains a unique CVE ID, description in the following format: [PROBLEM TYPE] in [PRODUCT/VERSION] causes [IMPACT] when [ATTACK], and at least 1 public reference.
- The Common Vulnerability Scoring System (CVSS) captures the principal characteristics of a vulnerability and produces a numerical score between 0 to 10 reflecting its severity (low, medium, high, critical).
- The Common Weakness Enumeration (CWE) is a list of common software and hardware weaknesses, classified precisely so that we can identify common patterns which can help us communicate about them. There can exist a one:many mapping between a CWE and a CVE.
- Just like CVSS provides severity scores to CVEs, the Common Weakness Scoring System (CWSS) ranks the severity of CWEs.
Finally, as you have learned, these systems do not exist in isolation, but work together to inform organizations, tools and services about vulnerabilities and their root causes.
If you made it this far, thanks for reading!
If you see any mistakes in this article, please let me know in the comments. I am not a security expert, but someone who is trying to educate herself about security, so your feedback is much appreciated :)
Lastly, a very important question for you:
If I had a dollar for every time I said vulnerability in this blog, how much money will I have by the end of this post?
